How to Use Trezor Wallet Login v24.12.3
In today’s digital age, securing your cryptocurrency assets is more critical than ever. Trezor Wallet is one of the most trusted hardware wallets that ensures the safety of your crypto holdings. With the latest Trezor Wallet Login v24.12.3, users can access their funds efficiently while maintaining top-level security. This blog will guide you through every aspect of using Trezor Wallet Login, ensuring a smooth and secure experience.
What is Trezor Wallet Login?
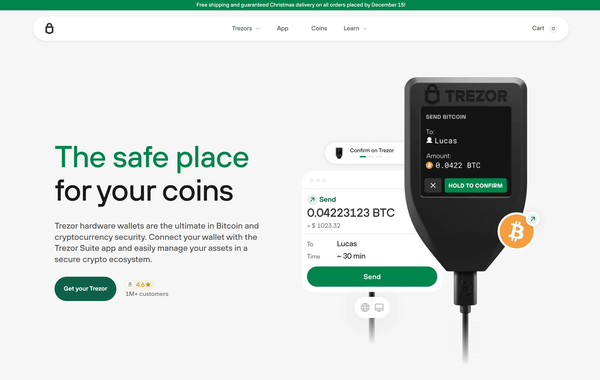
Trezor Wallet Login is the gateway to your Trezor hardware wallet. It allows you to securely access your cryptocurrency portfolio, manage assets, and perform transactions without compromising your private keys. Unlike software wallets, Trezor keeps your private keys offline, making it highly resistant to hacks and malware. The latest v24.12.3 update enhances the login process, providing a faster and more intuitive user interface while maintaining high security standards.
Step-by-Step Guide to Trezor Wallet Login v24.12.3
- Download Trezor Bridge:
To begin, you must have Trezor Bridge installed on your computer. Trezor Bridge is a small software that allows your device to communicate with your browser securely. You can download it directly from the official Trezor website: Trezor Bridge Download. - Connect Your Trezor Device:
Plug your Trezor hardware wallet into your computer using a USB cable. Ensure that your device is powered on and functioning correctly. - Access the Trezor Wallet Interface:
Open your preferred browser and navigate to the Trezor web wallet interface. The system will detect your connected device and prompt you for login. - Enter Your PIN:
Your Trezor device uses a PIN for an extra layer of security. Enter your PIN directly on the device, not on your computer, to prevent any potential keyloggers from capturing it. - Passphrase (Optional):
If you have enabled a passphrase for added security, you will be prompted to enter it. This is an optional but highly recommended feature for users with large crypto holdings. - Access Your Wallet:
Once the PIN and passphrase (if used) are verified, you will gain access to your wallet. You can now view balances, send or receive cryptocurrencies, and manage multiple accounts.
Key Features of Trezor Wallet Login
- High Security: Private keys never leave the device.
- User-Friendly Interface: The v24.12.3 update ensures a simple and smooth login experience.
- Cross-Platform Support: Compatible with Windows, macOS, and Linux.
- Backup & Recovery: Supports secure seed phrases to recover your wallet in case of device loss.
Tips for Safe Login
- Always download Trezor Bridge from the official website.
- Avoid using public or shared computers for wallet access.
- Regularly update your Trezor firmware and wallet software.
In conclusion, Trezor Wallet Login v24.12.3 combines top-notch security with user convenience, making it ideal for both beginners and advanced crypto users. By following the steps outlined above, you can safely access and manage your cryptocurrency portfolio without worrying about security breaches.
For more information and official guidance, visit the Trezor official website: https://trezor.io/start.